Autant pour moi, un nmap c'est juste un sniffer de port, mais tu peux également récupérer les trames de la pile OSI et tracer le protocole Ethernet par exemple avec un wireshark, tu récupères tout avec ça.
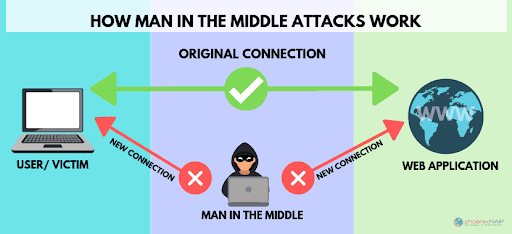
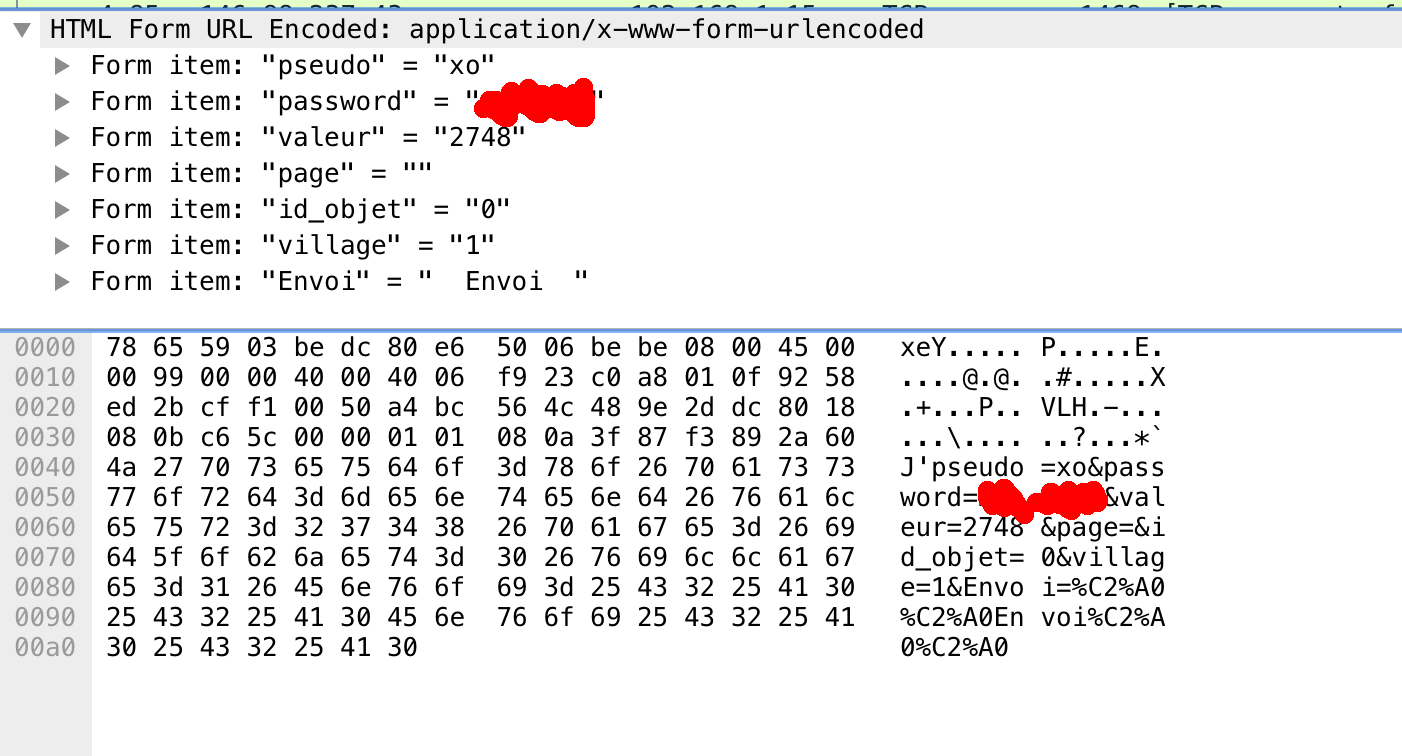
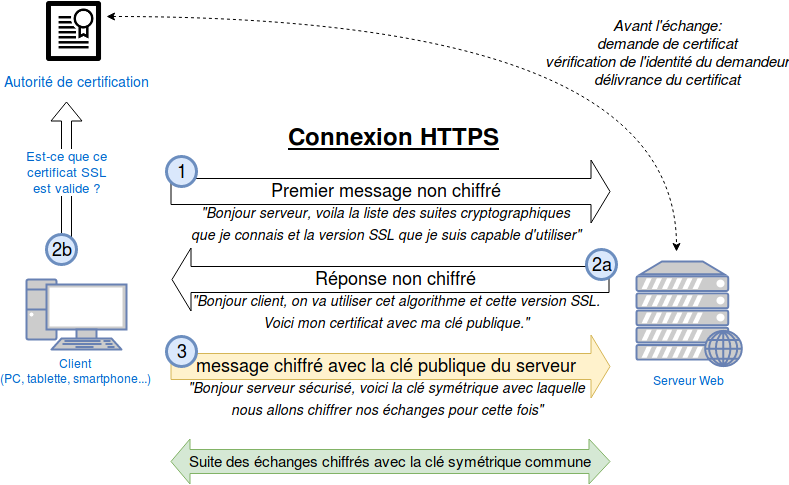
Man-in-the-middle c'est une attaque qui utilise les failles d'un réseau local pour "écouter" ce qui transit sur le réseau. En gros "l'homme au milieu" détourne le trafic et le consulte à loisir. Si le trafic est en clair, c'est à dire en http (et non https), les messages sont en clair.
exemple nmap, pour tracer toutes les ip locales d'un réseau :
pme@///: $ nmap -T4 -sP 192.168.1.0/24
Starting Nmap 6.46 (
http://nmap.org ) at 2020-04-30 19:28 CEST
Nmap scan report for 192.168.1.1
Host is up (0.013s latency).
Nmap scan report for ///.local (192.168.1.2)
Host is up (0.012s latency).
Nmap scan report for 192.168.1.3
Host is up (0.013s latency).
Nmap scan report for /// (192.168.1.4)
Host is up (0.057s latency).
Nmap scan report for /// (192.168.1.5)
Host is up (0.012s latency).
Nmap scan report for /// (192.168.1.6)
Host is up (0.055s latency).
Nmap scan report for ///.local (192.168.1.15)
Host is up (0.00041s latency).
Nmap scan report for ///.local (192.168.1.41)
Host is up (0.038s latency).
Nmap scan report for ///.local (192.168.1.254)
Host is up (0.0057s latency).
Nmap done: 256 IP addresses (9 hosts up) scanned in 3.67 seconds
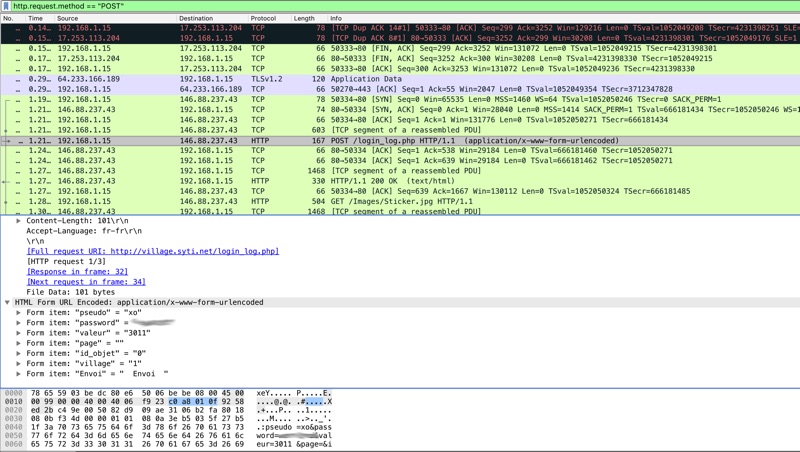
Capture sur interface en0 :
root@///: # tshark -i en0
Capturing on 'Wi-Fi'
1 0.000000 192.168.1.15 ? 179.60.192.3 TLSv1.2 98 Application Data
2 0.041044 179.60.192.3 ? 192.168.1.15 TLSv1.2 94 Application Data
3 0.041127 192.168.1.15 ? 179.60.192.3 TCP 66 63540?443 [ACK] Seq=33 Ack=29 Win=2047 Len=0 TSval=1049448725 TSecr=2767787654
4 0.265657 Quantenn_00:00:00 ? Spanning-tree-(for-bridges)_00 STP 60 Conf. Root = 0/4000/00:26:86:00:00:00 Cost = 0 Port = 0x8001
5 0.309353 Quantenn_00:00:00 ? Broadcast 0x7373 121 Ethernet II
6 0.573551 192.0.80.242 ? 192.168.1.15 TLSv1.2 1506 Server Hello, Change Cipher Spec, Application Data
7 0.675905 192.168.1.15 ? 192.0.80.242 TCP 54 49794?443 [ACK] Seq=1 Ack=1453 Win=4096 Len=0
8 0.733127 52.218.109.195 ? 192.168.1.15 TLSv1.2 85 Encrypted Alert
9 0.733224 192.168.1.15 ? 52.218.109.195 TCP 54 49793?443 [ACK] Seq=1 Ack=32 Win=4095 Len=0
10 0.734105 192.168.1.15 ? 52.218.109.195 TLSv1.2 85 Encrypted Alert
11 0.734160 192.168.1.15 ? 52.218.109.195 TCP 54 49793?443 [FIN, ACK] Seq=32 Ack=32 Win=4096 Len=0
12 0.771921 52.218.109.195 ? 192.168.1.15 TCP 60 443?49793 [ACK] Seq=32 Ack=32 Win=124 Len=0
13 0.771927 52.218.109.195 ? 192.168.1.15 TCP 60 443?49793 [FIN, ACK] Seq=32 Ack=33 Win=124 Len=0
14 0.772012 192.168.1.15 ? 52.218.109.195 TCP 54 49793?443 [ACK] Seq=33 Ack=33 Win=4096 Len=0
15 1.085547 192.0.80.242 ? 192.168.1.15 TCP 1506 [TCP segment of a reassembled PDU]
16 1.186338 192.168.1.15 ? 192.0.80.242 TCP 54 49794?443 [ACK] Seq=1 Ack=2905 Win=4096 Len=0
17 1.187328 Quantenn_00:00:00 ? Spanning-tree-(for-bridges)_00 STP 60 Conf. Root = 0/4000/00:26:86:00:00:00 Cost = 0 Port = 0x8001
18 1.288453 192.168.1.15 ? 34.237.73.95 TLSv1.2 354 Application Data
19 1.392419 Quantenn_00:00:00 ? Broadcast 0x7373 121 Ethernet II
20 1.481247 34.237.73.95 ? 192.168.1.15 TCP 66 443?59963 [ACK] Seq=1 Ack=289 Win=1025 Len=0 TSval=3324335813 TSecr=1049449966
21 1.481253 34.237.73.95 ? 192.168.1.15 TLSv1.2 391 Application Data
22 1.481359 192.168.1.15 ? 34.237.73.95 TCP 66 59963?443 [ACK] Seq=289 Ack=326 Win=2042 Len=0 TSval=1049450159 TSecr=3324335813
23 1.508285 192.0.80.242 ? 192.168.1.15 TCP 1442 [TCP Previous segment not captured] [TCP segment of a reassembled PDU]Application Data, Application Data
24 1.508386 192.168.1.15 ? 192.0.80.242 TCP 54 [TCP Dup ACK 16#1] 49794?443 [ACK] Seq=1 Ack=2905 Win=4096 Len=0
25 2.007200 192.0.80.242 ? 192.168.1.15 TCP 1506 [TCP Retransmission] 443?49794 [ACK] Seq=2905 Ack=1 Win=60 Len=1452
26 2.007272 192.168.1.15 ? 192.0.80.242 TCP 54 49794?443 [ACK] Seq=1 Ack=5745 Win=4051 Len=0
27 2.011012 192.168.1.15 ? 192.0.80.242 TLSv1.2 118 Change Cipher Spec, Application Data
28 2.011542 192.168.1.15 ? 192.0.80.242 TLSv1.2 224 Application Data
(...)